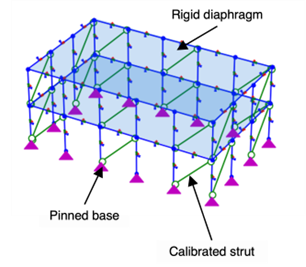
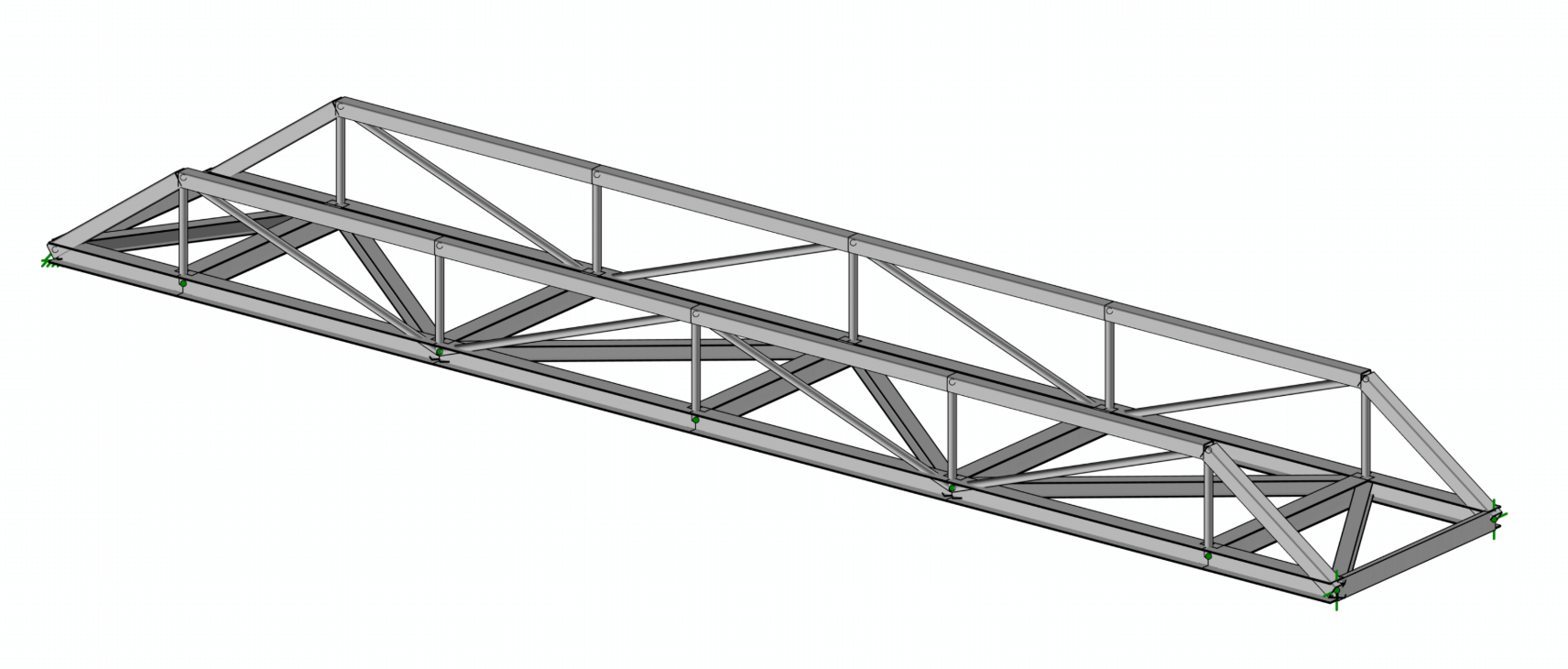
Research Team: Scott Hamel, PE, PhD, and Polly Murray, PhD Summary: Building code compliance varies widely […]
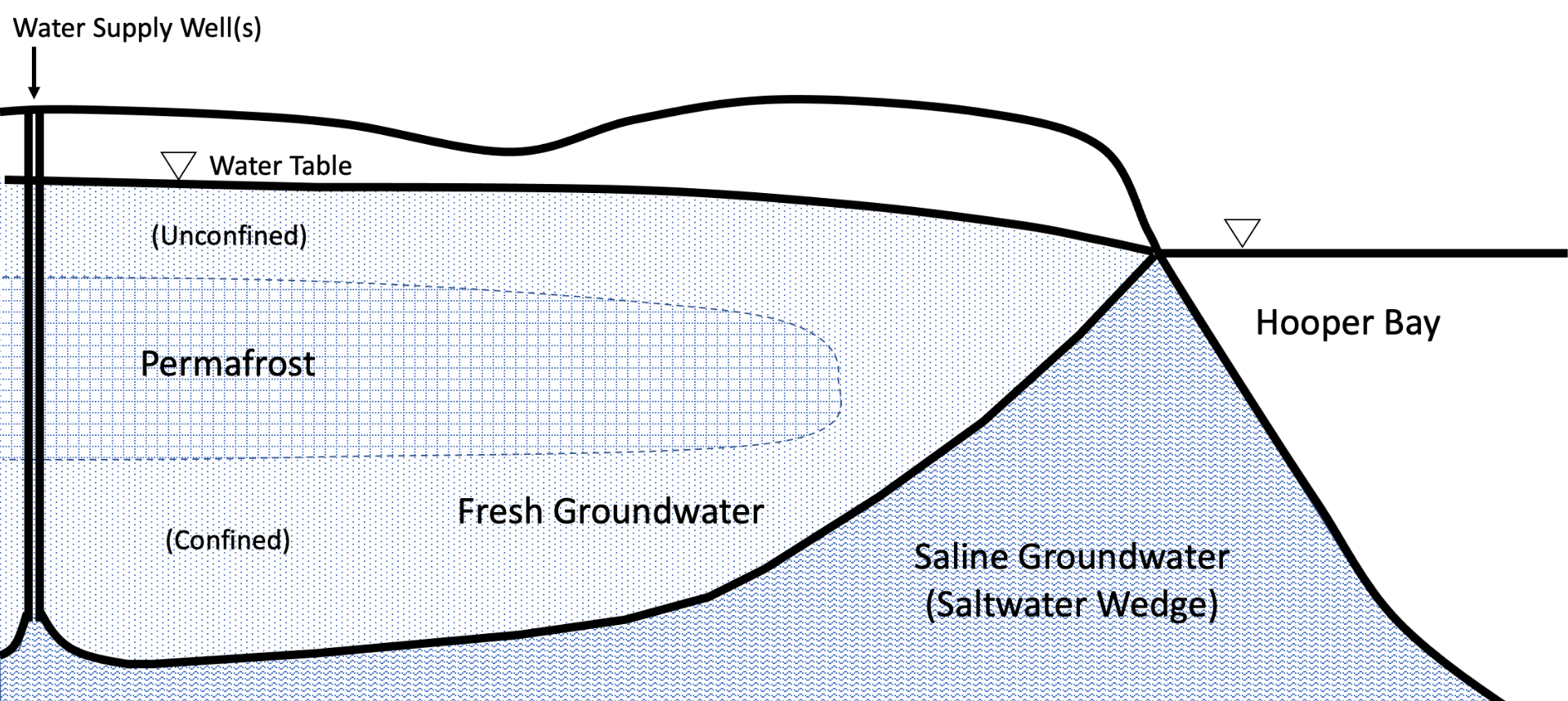
Student Members: Matthew Hegland Faculty Advisors: Dr. Thomas Ravens Description: A preliminary assessment of applying injection […]
Student Members: Nicholas Schwantes Faculty Advisors: Dr. Scott Hamel Abstract: The Iditarod National Historic Trail is […]
Research Team: Tristan A. Goers, Researcher, University of Alaska Anchorage Dr. Caixia Wang, Mentor, University of […]
Research Team: Mohammad Heidari Kapourchali, University of Alaska Anchorage Matthew Berman, University of Alaska Anchorage Micah […]
Research Team: Tyler Cushman, Graduate Student, University of Alaska Anchorage Dr. Raghu Srinivasan, Mentor, University of […]
This project seeks to extend the Arctic Vessel Monitoring Geofencing/Alert Awareness project, initially funded in ADAC Program Year 5, by providing enhanced command and control features that improve on the original goals of monitoring and alert awareness developed for the unclassified Marine Exchange PACTRACS system (which is a commercial mariner application).
Research Team: Gennady Gienko, Rob Lang, Scott Hamel, Kurt Meehleis, Tommy Folan Summary: In Alaska during […]
Tom Ravens and research assistant Jon Allen are developing a storm surge modeling system to examine […]
Tom Ravens and graduate student Garrett Yager completed a study (funded by the North Pacific Research Board) addressing the hydrodynamic and sediment transport impacts of the Endicott causeway on the North Slope of Alaska. Solid-filled causeways have been used along the Beaufort Sea coastline to support oil and gas drilling operations and to provide maritime access on a shallow coast.