Real-time continuous iris recognition for authentication using an eye tracker


Advancing Authentication: The Promise of Iris Recognition
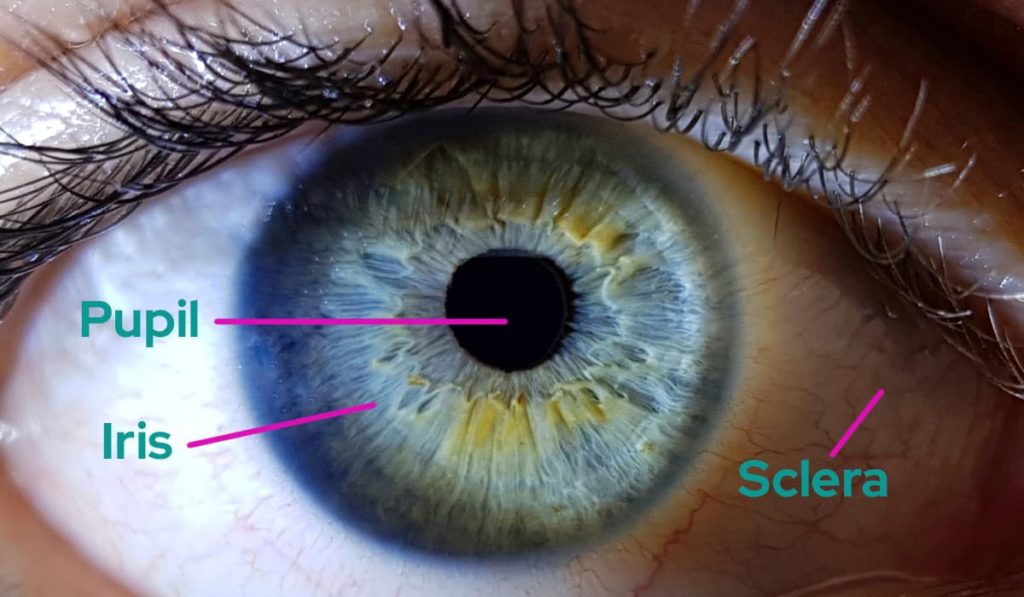
In recent research, a team of UAA experts explored whether a commercial eye tracker can be used for unobtrusive, continuous, real-time user authentication via iris recognition. This innovative approach leverages the unique patterns within the iris, which are highly distinctive and stable over time.
While traditional authentication methods require periodic user input, continuous iris recognition could provide ongoing verification without disrupting the user's workflow. This technology has the potential to significantly enhance security in various applications, from enterprise systems to healthcare and financial services.
As eye tracking technology continues to advance, its capabilities for multiple factor, continuous authentication are becoming increasingly compelling.
Frequently Asked Questions
Continuous iris recognition is an authentication method that uses the unique patterns of a person's iris to verify their identity in real-time and on an ongoing basis, without requiring any specific action from the user.
This system uses a commercial eye tracker to capture images of the iris. The unique patterns within the iris are then analyzed to continuously verify the user's identity.
Continuous authentication provides a higher level of security compared to traditional, one-time authentication methods like passwords or fingerprint scans. It ensures ongoing verification, reducing the risk of unauthorized access.
Enhanced Security: Continuous verification makes it more difficult for unauthorized users to gain access.
Unobtrusive Authentication: Iris recognition can be performed without requiring any specific action from the user, minimizing disruption to their workflow.
Real-time Verification: Identity is continuously verified, providing immediate alerts if unauthorized access is detected.
This technology has potential applications in various fields, including:
Enterprise systems
Healthcare
Financial services
Yes, the patterns within the iris are highly distinctive and stable over time, making iris recognition a very secure method of authentication.
Eye-tracking technology enables the unobtrusive and continuous capture of iris images, making real-time iris recognition possible without disrupting the user.
This collaborative project is led by Kenrick Mock, Bogdan Hoanca, Justin Weaver, and Mikal Milton at the UAA College of Engineering.
